Cyber Threat Landscape: A Deep and Practical Overview

Introduction to the Cyber Threat Landscape
In today’s digital world, cyber threats are growing faster than ever. As businesses, governments, and individuals depend more on the internet, cloud services, mobile devices, and digital payments, attackers are also becoming smarter and more aggressive.
The Cyber Threat Landscape refers to the complete picture of existing and emerging cyber threats, including:
- Who is attacking
- What techniques they are using
- Which systems are being targeted
- Why these attacks are happening
Understanding this landscape is critical for protecting data, systems, and digital identities.
What Is a Cyber Threat?
A cyber threat is any potential danger that can exploit weaknesses in computer systems, networks, or applications to cause harm.
A cyber threat can:
- Steal sensitive data
- Damage or destroy systems
- Disrupt services
- Cause financial or reputational loss
You can also read : Cyber Security Explained In Simple Words For Beginners
Common Targets
- Individuals (personal data, bank details)
- Businesses (customer data, intellectual property)
- Governments (national security systems)
- Critical infrastructure (hospitals, power grids, transport)
Major Types of Cyber Threats
1. Malware Attacks
Malware means malicious software designed to harm systems or steal data.
Common Types of Malware:
- Virus – Attaches to files and spreads when opened
- Worm – Spreads automatically through networks
- Trojan Horse – Looks like legitimate software but is harmful
- Spyware – Secretly monitors user activity
- Adware – Displays unwanted advertisements
📌 Example: Downloading cracked software from unknown websites.
2. Ransomware Attacks
Ransomware encrypts files and demands money to unlock them.
How it works:
- Victim clicks a malicious link or attachment
- Files get encrypted
- Attacker demands ransom (usually cryptocurrency)
Impact:
- Data loss
- Business downtime
- Financial damage
📌 Real-world impact: Hospitals, companies, and even government systems have been forced offline due to ransomware.
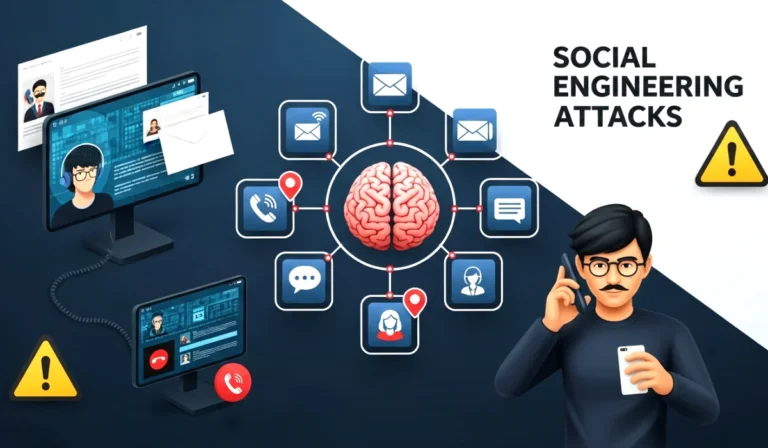
3. Phishing and Social Engineering Attacks
These attacks target human psychology, not technology.
Types of Phishing:
- Email phishing – Fake emails pretending to be trusted sources
- Smishing – Phishing via SMS
- Vishing – Voice calls to steal information
- Spear phishing – Targeted attacks on specific individuals
📌 Goal: Steal passwords, OTPs, or financial details.
4. Denial of Service (DoS & DDoS) Attacks
These attacks overload a system with traffic, making it unavailable.
- DoS – Attack from a single system
- DDoS – Attack from thousands of compromised devices
Effects:
- Website crashes
- Service downtime
- Loss of customers and trust
5. Man-in-the-Middle (MITM) Attacks
In this attack, the attacker secretly intercepts communication between two parties.
Common scenarios:
- Public Wi-Fi networks
- Fake access points
- Unsecured connections
📌 Risk: Sensitive data like passwords and credit card details can be stolen.
6. Zero-Day Exploits
A zero-day vulnerability is a software flaw unknown to the vendor.
Why dangerous?
- No patch available
- Attackers exploit it before anyone knows
📌 These attacks are often used in advanced and targeted cyber attacks.
Modern and Emerging Cyber Threats
1. AI-Powered Cyber Attacks
Attackers now use AI to:
- Create realistic phishing emails
- Crack passwords faster
- Automate large-scale attacks
AI makes cyber attacks faster, smarter, and harder to detect.
2. Internet of Things (IoT) Threats
Smart devices like:
- CCTV cameras
- Smart TVs
- Smart home devices
often have weak security, making them easy targets.
📌 Compromised IoT devices are commonly used in DDoS attacks.
3. Cloud Security Threats
As businesses move to cloud platforms, new risks appear:
- Misconfigured storage
- Weak access controls
- Insecure APIs
📌 A single misconfiguration can expose millions of records.
4. Deepfake and Identity Fraud
Attackers use deepfake technology to:
- Fake voice calls
- Create fake videos
- Impersonate executives
📌 This is increasingly used in financial fraud and corporate scams.
Threat Actors: Who Is Behind Cyber Attacks?
1. Cybercriminals
- Motivated by money
- Focus on fraud, ransomware, and data theft
2. Hacktivists
- Politically or ideologically motivated
- Target governments or corporations
3. Insider Threats
- Employees or contractors
- Often accidental, sometimes malicious
4. Nation-State Attackers
- Highly skilled
- Target critical infrastructure and intelligence systems
Why Understanding the Cyber Threat Landscape Matters
Understanding cyber threats helps:
- Improve security planning
- Reduce attack risks
- Protect sensitive data
- Ensure business continuity
- Build trust with users and customers
Cybersecurity is no longer optional — it is a necessity.
How to Reduce Cyber Threat Risks
Best Practices:
- Regular software updates
- Strong passwords and MFA
- Employee awareness training
- Secure backups
- Network monitoring
- Zero Trust security model
Conclusion
The Cyber Threat Landscape is constantly evolving. Attackers adapt quickly, and new threats appear every day. Organizations and individuals must stay informed, proactive, and prepared.
Cybersecurity is not just about technology — it is about awareness, discipline, and continuous improvement.




One Comment